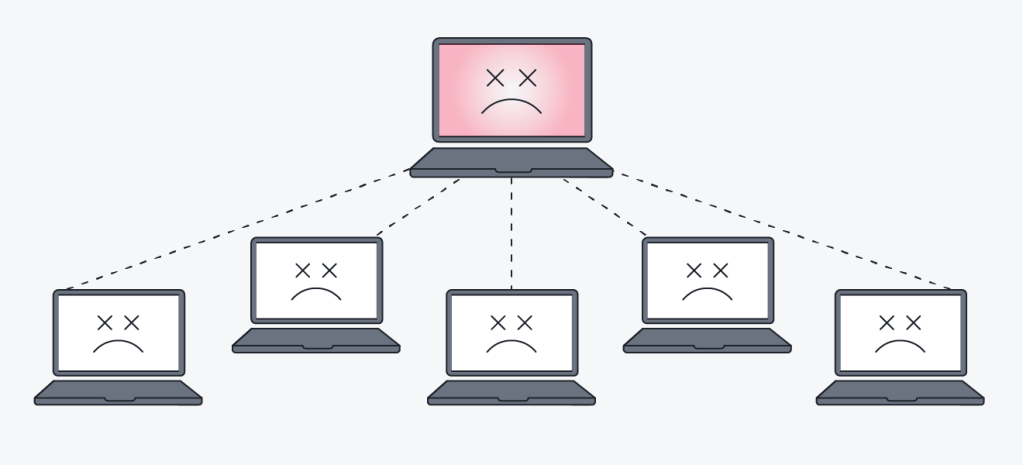
A botnet is a collection of compromised devices that have often become infected with malware. These devices operate under the control of a hacker or cybercriminal, forming a vast network of “bots” that can perform various malicious activities.
These bots can be utilized to launch large-scale cyberattacks, including Distributed Denial of Service (DDoS) attacks, which overwhelm targeted systems by flooding them with traffic. In addition to DDoS attacks, botnets are used to send out massive amounts of spam emails, steal sensitive data like personal information and financial credentials, or mine cryptocurrencies, which can be highly profitable for cybercriminals.
Botnets are particularly insidious because they spread by exploiting vulnerabilities within software systems or by tricking users into downloading malicious files, often through phishing scams or deceptive advertisements. Once a device becomes part of a botnet, it can be remotely controlled by the attacker without the user’s knowledge, enabling wide-reaching criminal activities.
The distributed nature of botnets makes them exceptionally difficult to detect and eradicate. Traditional cybersecurity measures may struggle to identify and neutralize these threats, as compromised devices can be located across various regions and managed by different individuals. Cybersecurity protection is, therefore, essential for both individuals and organizations to prevent becoming victims of these formidable cyber threats. Continuous monitoring, regular updates, and user education are vital strategies in safeguarding against botnet infections.



Leave a comment